
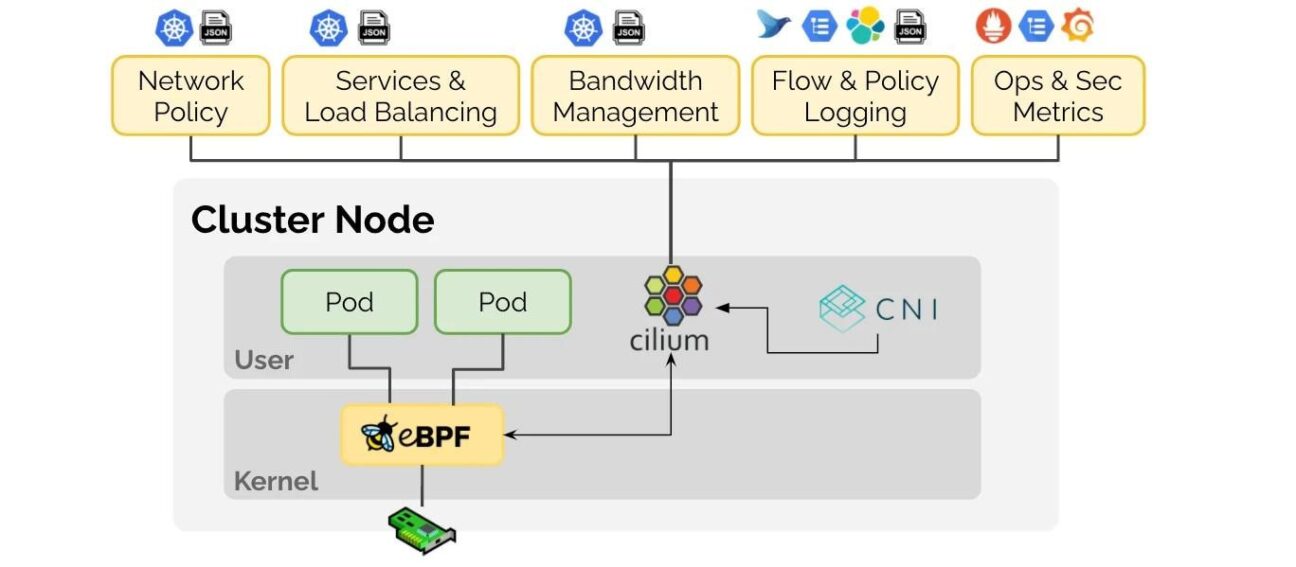
Cilium and eBPF
Cilium is built on top of eBPF for it to provide security and observability within the cluster. Extended Berkeley Packet Filter (eBPF) is a Linux kernel technology (starting at kernel 3.15) which allows it to run programs without having to change the kernel source code or adding additional modules. You can think of it as a lightweight, sandboxed virtual machine inside the Linux kernel where you can run eBPF code that can take advantage of specific kernel resources.
For our use case during the Tech Friday, we explored Cilium by securing a weather app. The pod for the weather app fetches its data from the internet using the OpenWeatherMap API. This can be a common use case where certain pods within the cluster need to have access to the outside world. We want to make sure that the pods can only reach the intended target API (api.openweathermap.org) and no other potentially malicious endpoint.
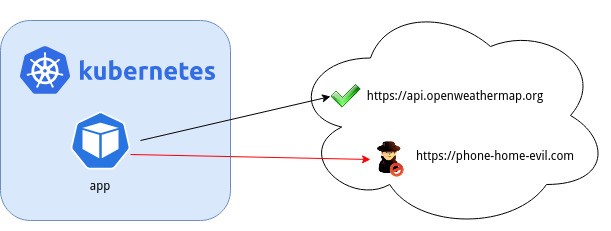
Instead of writing firewall rules, or using other third party tools, which may be resource heavy, Cilium can be used as a lightweight solution that leverages eBPF to implement security policies, which harden our application at the network layer. Since it can hook into the kernel, it has great visibility of what goes on at the network level. With a few lines of code and a nifty online policy editor, it was quite easy to create a security policy to allow our app to only reach the intended endpoints.
In the visual editor, we can easily specify the details of the application (i.e. in which namespace it runs, and to which endpoint and port it should only have access to).
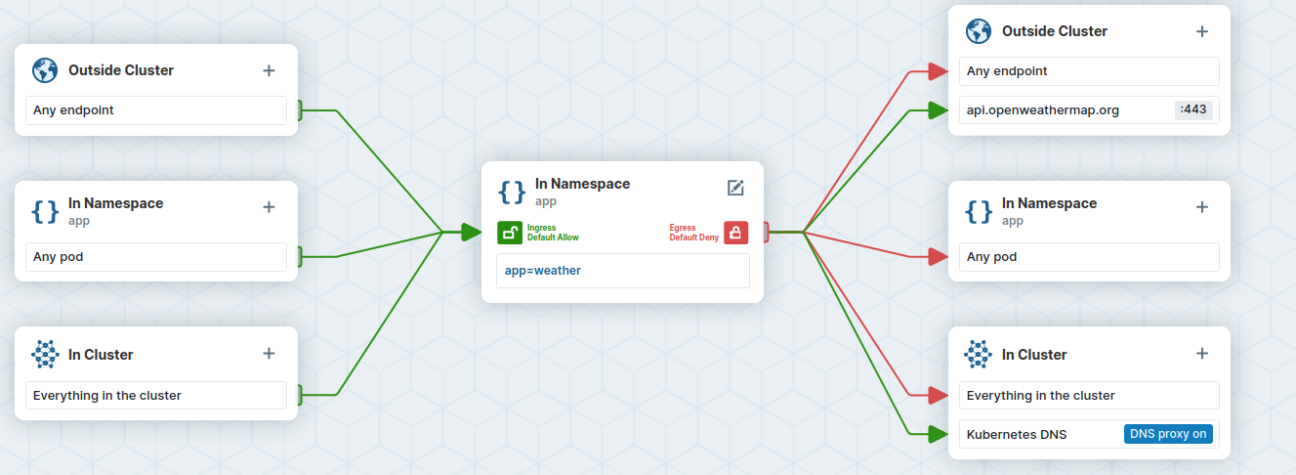
In the policy editor, we can define our rule, which will provide a manifest, which we can apply to the cluster. Once applied we observed that access to any other endpoint other than the OpenWeatherMap API was indeed being dropped.
The future is eBPF
eBPF has emerged and provides greater flexibility for Linux (whether running on premise, in the cloud, on Kubernetes), and with tools like Cilium we can see how to quickly setup networking policies to secure our environment. For those who also want to get their hands dirty, the Tech Friday Cilium project can be found on our GitHub page.
Innovative Tech
The Innovative Tech (I-Tech) team consists of 50+ consultants working with Elastic, Atlassian, Red Hat & Java technologies. They work on customer solutions around monitoring, software team collaboration, DevOps, automation, CICD and software development. Everything to take a customer to the next level of innovation, based on platforms. Would you like to work in the I-Tech team at Devoteam, check out our page and perhaps you will find a fitting career path within the company!