Introduction
These days, we have an extensive list of Ingress controllers in the market, each with their particular performance, complexity, management, scalability and pros and cons. From the moment that we decide to move to any Cloud provider, it’s very important to make use of all resources that it offers as long as the resource fits your needs. With this you can have a reliable, manageable and scalable infrastructure. Speaking about Ingress controllers and Cloud providers, I want to point out the Application Gateway Ingress Controller (AGIC).
The main idea of an Ingress Controller
You decided to move your deployment to K8s and you want to expose it through a service in order to give access to the clients, right?! it’s fine, you can even expose the service to the internet. However, by doing that, you are going to end up with a solution that is not sustainable, not manageable, very limited and not safe, in other words, it’s not advisable at all.
With Ingress you can receive the requests from the clients, provide a domain name to your service, routing path, and expose it to the internet. Wow, that’s amazing, this is what you were looking for, right?
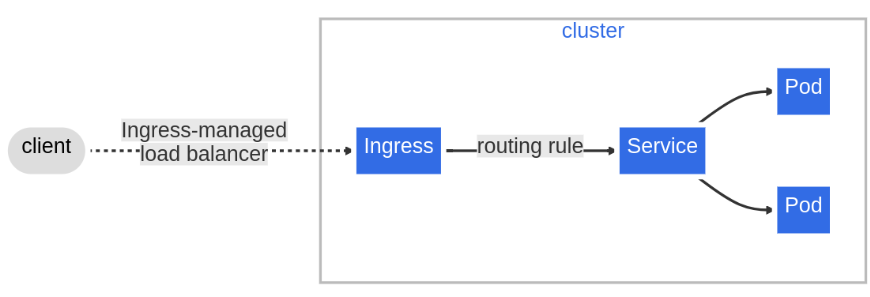
Now, you have your Ingress controller receiving all the traffic, encrypting and decrypting Transport Layer Security (TLS), and performing the correct balance by distributing it to the services.
Well, you just noticed that the number of clients has increased, your exposure is getting risky and your Ingress is demanding a huge computing process for encrypt and decrypt. This is something you need to resolve. By doing some of your research, you found Azure Application Ingress Controller.
Azure Application Gateway Ingres Controller
Azure Application Gateway Ingress controller, AGIC, runs on its pods on your AKS cluster and works on layer 7, load balance. It enables you to manage traffic to your applications, pretty similar to what we just mentioned above, right?
However, now we have a better escalation and secure environment.
With AGIC you will have the following features:
- URL routing, Cookie-based affinity;
- TLS termination;
- End-to-end TLS;
- Support for public, private and hybrid environments;
- Web Application Firewall.
AGIC will also interact with your inbound traffic by increasing or decreasing the load scale, without impact on any of the resources in your AKS cluster. That is perfect.
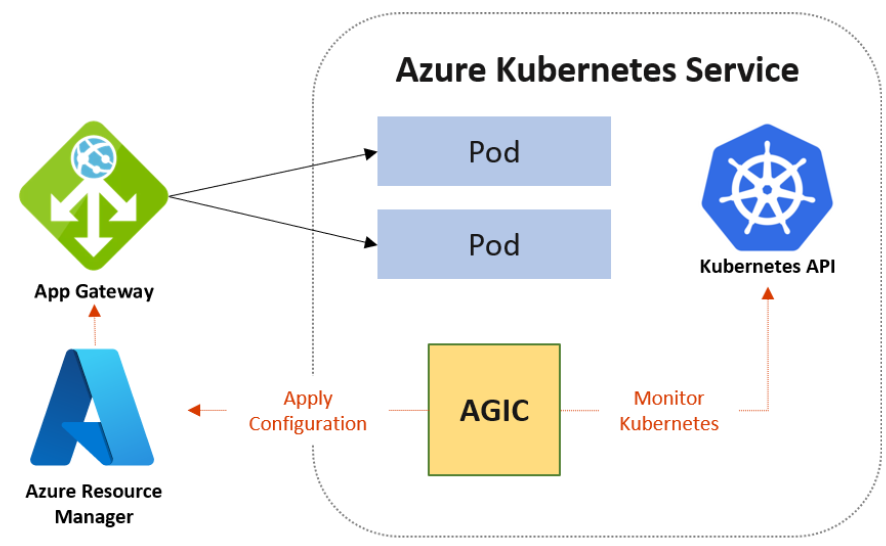
How do I configure it?
There are 3 different methods that you can use to deploy such a solution.
From scratch
By deploying a new AKS, an application gateway and enabling appingress-appgw add-on in it.
Using the current AKS deployment and a new Application Gateway
By enabling the ingress-appgw add-on on the current AKS and deploying a new AGW.
Using Helm charts
By installing the chart in your current AKS deployment.
Assuming that you already have Azure CLI installed, you will notice that I am using environment variables, this was declared on my operating system Ubuntu 22.04. Everything can be done via Portal, however we will cover the second option using your current AKS deployment via Azure cli.
- Create a public IP
- az network public-ip create -n $pipName -g $rgName -l $location –allocation-method Static –sku Standard.
- Create a vnet
- Here you need to place your application gateway outside AKS vnet.
- az network vnet create -n $appgwVnetName -g $rgName -l $location –address-prefix 10.0.0.0/16
- –subnet-name $snetName –subnet-prefix 10.0.0.0/24.
- Here you need to place your application gateway outside AKS vnet.
- Create a WAF policy
- This is needed for the Application Gateway since we are going to deploy it with the sku of WAF_v2 that brings to us the WAF feature.
- az network application-gateway waf-policy create –name $wafPolicyName –resource-group $rgName.
- This is needed for the Application Gateway since we are going to deploy it with the sku of WAF_v2 that brings to us the WAF feature.
- Create the Application gateway
- This might take a few minutes, so you can go and grab a coffee.
- az network application-gateway create -n $appgwName -l westeurope -g $rgName –sku WAF_v2 –public-ip-address $pipName –vnet-name $appgwVnetName –subnet $snetName –priority 100 –waf-policy $wafPolicyName.
- This might take a few minutes, so you can go and grab a coffee.
- Enable add-on on AKS
- appgwId=$(az network application-gateway show -n $appgwName -g $rgName -o tsv –query “id”)
- az aks enable-addons -n $aksName -g $rgName -a ingress-appgw –appgw-id $appgwId.
- Create vnet peering
- As you saw above, we are creating a new vnet, which means that our new vnet cannot communicate with the AKS vnet. In order to fix it we will create a peering between them.
- aksVnetId=$(az network vnet show -n $aksVnetName -g $rgName -o tsv –query “id”)
- az network vnet peering create -n AppGWtoAKSVnetPeering -g $rgName –vnet-name $appgwVnetName –remote-vnet $aksVnetId –allow-vnet-access.
- appGWVnetId=$(az network vnet show -n $appgwVnetName -g $rgName -o tsv –query “id”)
- az network vnet peering create -n AKStoAppGWVnetPeering -g $rgName –vnet-name $aksVnetName –remote-vnet $appGWVnetId –allow-vnet-access .
- As you saw above, we are creating a new vnet, which means that our new vnet cannot communicate with the AKS vnet. In order to fix it we will create a peering between them.
- Create an application deployment
- To make our life easier I prepared a web server deployment. Feel free to use it.
- git clone https://github.com/lopes221/aksAppGatewayIngressController.git
- cd deployments
- kubectl create namespace nginx
- kubectl apply -f nginx-deployment.yaml -n nginx
- kubectl apply -f nginx-service.yaml -n nginx
- kubectl apply -f nginx-ingress.yaml -n nginx
- To make our life easier I prepared a web server deployment. Feel free to use it.
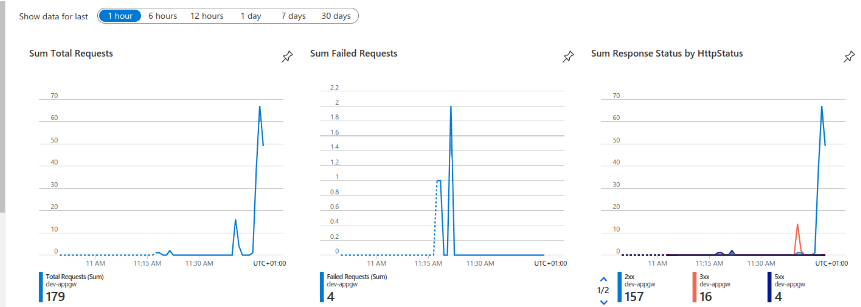
By concluding all the steps above, you should be able to see your application traffic going through the Azure Application Gateway Ingress Controller. Please have a look at the image below.
Final thoughts
Azure Application Gateway Ingress Controller is very powerful with multiple features and scalability. In terms of security, we managed to see in the graph above that we implemented using the Azure Sku WAF_v2 of Application Gateway, which provides us a WAF ( Web Firewall Application), making our environment way safer and scalable.
Of course we need to set more WAF rules but this will depend on each environment and here we have the fundamentals that will give you the base to your implementation.
In other words, AGIC is totally worth implementing in your environments.