What is Anypoint Virtual Private Cloud?
Anypoint Virtual Private Cloud (VPC) allows you to create logical or isolated networks in the cloud where you can deploy or run the resources securely. MuleSoft CloudHub is a multi-tenant integration platform as a service. Anypoint VPC allows you to create an isolated network where you can host the workers or Mule applications. A worker is basically a virtual machine (AWS EC2 Instances) which comprises an operating system, Java Virtual Machine, Mule Runtime, and applications.
By default when no VPC is created, CloudHub workers are deployed to Global Cloud workers which are the public network segment of the CloudHub network. It exposes the two DNS for your application:
- <app-name>.region.cloudhub.io to access applications directly over shared load balancer.
- mule-worker-<app-name>.region.cloudhub.io to access workers directly.
Anypoint Virtual Private Cloud allows you to extend your corporate network and allows CloudHub workers to connect resources behind the firewalls. VPC connects CloudHub workers to an on-premise data center using the below techniques:
- Secure VPN Tunnel (IPSec Tunneling)
- Private AWS using VPC Peering.
- AWS Direct Connect.
VPC CIDR Block Size
It is very important to decide on a CIDR (Classless Inter Dynamic Routing) mask before we create VPC’s. The smallest subnet mask you can assign to VPC is 0/24 (256 IP Addresses) and the largest subnet mask is 0/16 (65536 IP Addresses).
It is very important to select a higher or right range of CIDR masks because once VPC has been created, you cannot change the CIDR mask range. In case, if you want to increase the CIDR mask, you need to do a lot of work like deleting the VPC and recreating it again.
VPC Firewall Rules
It is important to define firewall rules to allow access to specific IP addresses and ports. By default, there are 4 firewall rules:
| Type | Port | Description |
| http.private.port | 8091 | Accessible within VPC over HTTP |
| https.private.port | 8092 | Accessible within VPC over HTTPS |
| http.port | 8081 | Accessible from anywhere or outside VPC over HTTP |
| https.port | 8082 | Accessible from anywhere or outside VPC over HTTPS |
VPC Region
It is very important to select the appropriate VPC region and mostly it is selected close to your corporate datacenters in case of VPN IPSec tunnelling or VPC peering in case of Anypoint VPC and AWS VPC exists in the same region.
VPC Business Groups
It is necessary to associate the Business Group with your Anypoint VPC and generally, it is recommended to create Anypoint VPC in the parent business group and share it with other sub-business groups.
Organization Administrators are responsible for creating the Anypoint VPC in the main business group and can share it with other child business groups.
VPC Environment
It is important to bind the environment with your Anypoint VPC. If you don’t select the environment, the application is deployed in the selected region of your Anypoint VPC.
It is recommended to create separate Anypoint VPC for Production and Non Production environments. All non-production environments like Development, SIT, UAT, QA can be mapped with non-production VPC and the production environment can be mapped with production VPC.
Connecting VPC to your Datacenter
It is possible to connect corporate, on-premise, or private cloud-hosted data centers using VPN IPSec Tunnelling. Using VPC Peering or AWS Direct Connect is also possible.
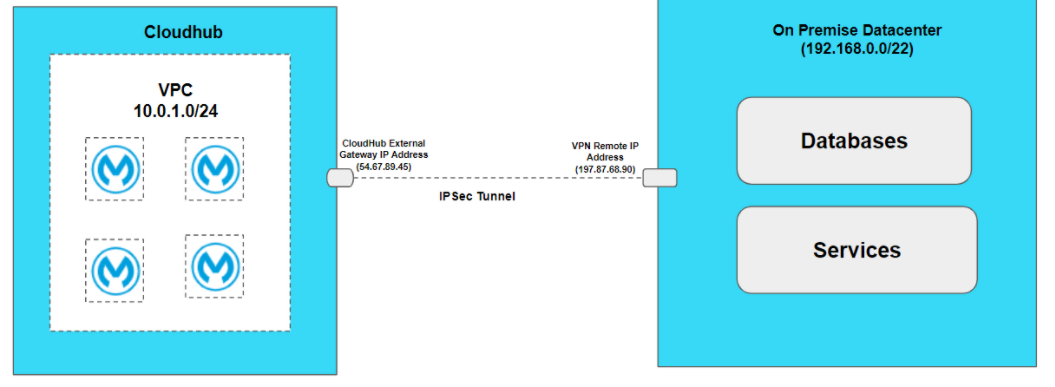
1. VPN IPSec Tunnelling
VPN IPSec Tunnelling can be used when you want network-to-network configuration for connecting an on-premise data center with Anypoint VPC.
VPN IPSec tunnel is a set of protocols or standards to establish a connection with an on-premise data center. IPSec tunnel is applied at the IP layer and it allows us to connect the entire network instead of a single device.
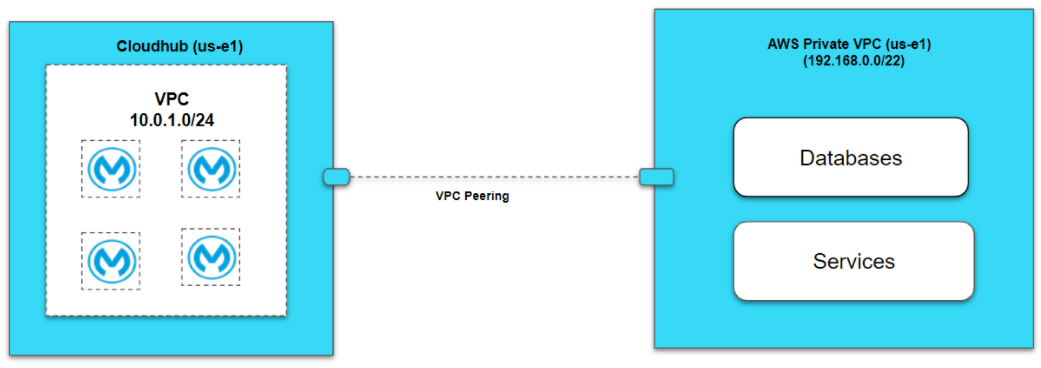
2. VPC Peering
VPC peering connects two VPCs. In this case, it pairs your private Amazon VPC directly to your Anypoint VPC. This enables you to route traffic between the two VPCs so they can communicate as though they are in the same network.
For VPC peering, ensure that Anypoint VPC and AWS Private VPC must exist in the same region.
3. Direct Connect
AWS Direct Connect lets you create a dedicated network connection between your network and one of the DX locations. Once you have established DX connectivity in an AWS account, you can establish connectivity with a CloudHub VPC.
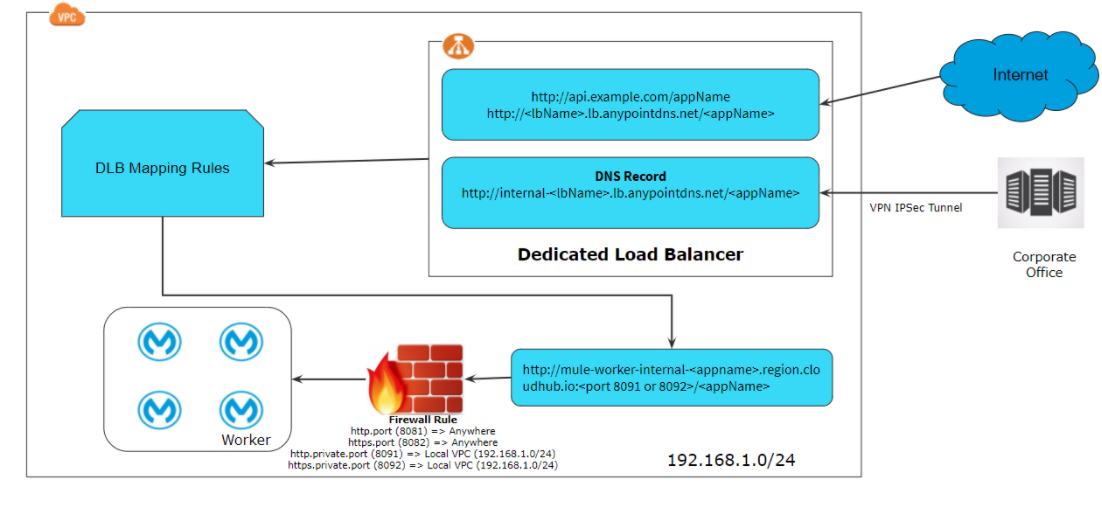
Accessing Application within VPC
For accessing applications within VPC, you can use the below URLs.
Port 8091: http://mule-worker-internal-<appname>.region.CloudHub.io:8091/
Port 8092: https://mule-worker-internal-<appname>.region.CloudHub.io:8092/
Creating AnyPoint VPC, VPN and DLB is self-service but you can request MuleSoft to create VPN IPSec tunneling, VPC Peering, or AWS Direct Connect by filling AnyPoint VPC discovery template.
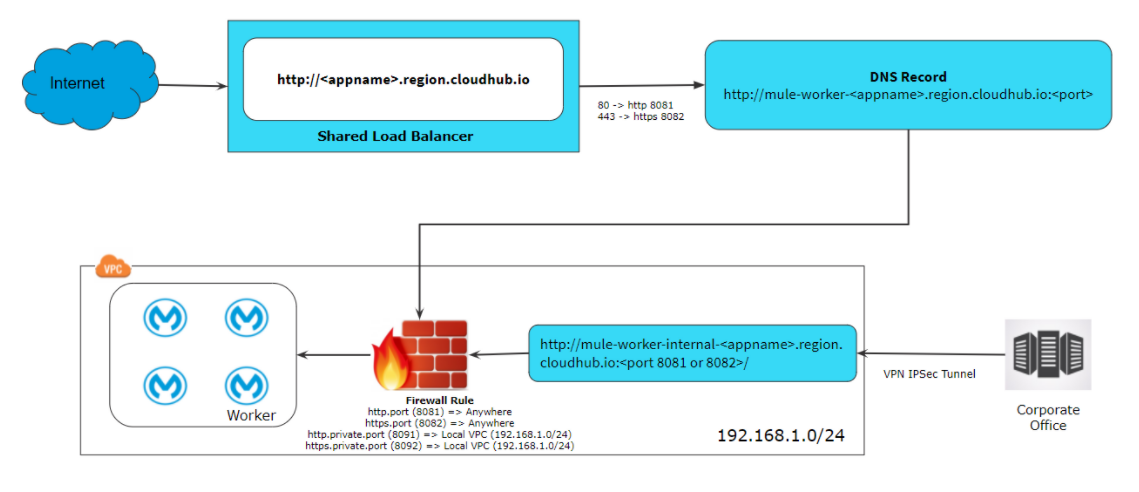
Accessing Application Over Public Internet When Deployed Within VPC
There are various ways that you can API’s over the public internet when an application is deployed within the VPC.
- Deploy the application on port 8081 (http.port) or 8082 (https.port), as per the above firewall rule these ports are accessible anywhere. So this APIs can be access using http://<appname>.region.CloudHub.io/ or https://<appname>.region.CloudHub.io/
- In case an application deployed on port 8091 (http.private.port) or 8092 (https.private.port), as per the above firewall rule these ports are accessible within VPC. So these APIs can be accessed on our public internet using a dedicated load balancer if your IP Address is whitelisted in DLB configurations.
VPC Use Cases
- To run the integration or API’s within secure networks or private subnets, you can deploy API within the VPC. For example, you have system APIs that are accessing backend databases and those APIs must be deployed within a secure or private network in CloudHub, so it is accessible by the applications deployed within the same VPC.
- For creating the dedicated load balancer, we need to create a VPC.
- For creating VPN IPSec tunneling, AWS Direct Connect, or VPC peering, we need to create a VPC.
VPC Recommendations
- Always create a VPC in the same region or near to your datacenter or AWS region (VPC peering).
- All non-prod environments like dev, test, sit can be mapped to non-prod vpc and production environment to prod vpc.
- Multiple environments can be mapped to the same VPC’s.
- Always choose a higher range of CIDR mask while doing VPC sizing as it is not possible to update CIDR mask later once VPC created.
- Always choose a CIDR mask that doesn’t overlap with your datacenter IP addresses or subnets.
- Always choose a VPC CIDR mask 10 times larger than expected application to be deployed per environment within VPC.
Conclusion
Anypoint VPC is a very important component in the MuleSoft ecosystem for creating isolated, secure network segments and there are many use cases as discussed above where there is a need for Anypoint Virtual Private Cloud.
At Devoteam, we support the clients to identify the use cases for implementing the Anypoint VPC in a secure manner with best practices and guidelines.
Our 25+ years of integration experience in projects within every sector you can think of, combined with a strong partnership with MuleSoft, enable us to guide your organization through every API-related challenge. Looking for help with setting up Anypoint iPaaS platforms, implementing Hybrid Architecture including Anypoint VPC, DLB, and VPN? Feel free to contact us and we’ll see how we can help each other.